Ezhednevnik pitaniya. Alternative Title: Peredvizhniki Society Peredvizhniki, (Russian: “The Wanderers”) group of Russian painters who in the second half of the 19th century rejected the restrictive and foreign-inspired classicism of the Russian Academy to form a new realist and nationalist art that would serve the common man. Believing that art should be useful, a vehicle for expressing humanitarian and social ideals, they produced realistic portrayals of inspiring or pathetic subjects from Russian middle-class and peasant life in a literal, easily understood style.
This does seem to be the case - the tools execute, device_infos returns some information, useful at least for a partial decryption of a physical image. Is it feasible to patch kernel memory once a jailbroken A5 device is already booted? Or would this require a modification to the Corona payload to apply the new kernel patch along with the others. I am waiting on some hardware to be able to start looking into this myself. In the meantime, any perspective on how to go about this would be greatly appreciated. Original comment by 0x56.0x6.@gmail.com on 29 Feb 2012 at 4:32.
Download ssh_rd_rev04b-iPhone4-RevA.jar from Mafia-download.com. This file ssh_rd_rev04b-iPhone4-RevA.jar is hosted at free file sharing service 4shared. If you are the copyright owner for this file, please Report Abuse to 4shared.
Grapple: First, install OpenSSH on the A5 device through Cydia. Then, use scp or sftp to upload the ramdisk tools (specifically, bruteforce and device_infos; restored_external doesn't matter here) and kernel_patcher (attachment in this issue) to the device. Once the files are uploaded, connect with ssh. Run kernel_patcher to gain access to the crypto engine, then you can run device_infos followed by bruteforce to generate the keys. I haven't quite figured out pulling an image, as the filesystem is mounted and active while the device is running (I pulled a dd image, but there were some issues with trying to decrypt it, probably because I was still using the phone while the image was running.). That is the general idea of what to do, hope it helps get you started. Simg: Unfortunately, without access to the GID key, the encrypted KBAGs cannot be decrypted.
By the time iBoot is finished and passes control to the kernel, the GID key is rendered inaccessible until a reboot of the device. The limera1n exploit allows running unsigned code at a stage in the boot process where the GID key is still accessible.
Corona (which Absinthe is used to inject on A5 devices) exploits the kernel, so by the time it takes place, the GID key is inaccessible. Tl;dr KBAG keys will not be available on A5 devices until a limera1n style exploit is discovered:) Original comment by 0x56.0x6.@gmail.com on 9 Mar 2012 at 7:18. I'm trying to recompile kernel_patcher.c for another purpose, but I can't get it to run on my device.
I'm in deep trouble here. Probably amateur problems for you guys. Short story- ipad 2 5.0.1 jb with absinthe. Wanted to use iUsers but realized after install it was for 4.x and lower. Uninstalled iUsers, caused springboard to crash every respring. Was planning to re-jb with absinthe however unable to jb because 'stash' is found.
I simply went into iFile, renamed 'stash' to 'stashs' then on the next respring i have gotten stuck on the apple logo. I would like to stay on 5.0.1 until 5.1 is jb'en. If anyone has a suggestion on what i can do- i would be greatly appreciative. Also, blobs saved but not working so my only alternative im aware of is restore n update (super sad face) thanks in advance. -mike Original comment by iDenver.@gmail.com on 2 Apr 2012 at 8:04.
Hi, I'm not an expert, but I can't stop here. I need to recover deleted photos and video from an iphone 4s. I already saved the rdisk0 image with ssh -p 2222 root@localhost dd if=/dev/rdisk0 bs=4096 dd of=iphoneraw and the keychain with keychain_dump so i got cert.plist genp.plist inet.plist keys.plist. Now i'm a little bit confused. I red that is not possible to recover deleted data using emf_decrypter but it's possible with emf_undelete. Could you tell me how i should use the emf_undelete script??
I need also to wipe the iphone and put a not jailbreak ios. So in order to this what else i should save from the iphone that will able me to recover deleted files in the future?
Something else like dd or keychain_dump?? Thanks in advance Original comment by andrei.m.@gmail.com on 7 Oct 2012 at 10:51. @jean.sig.@gmail.com i look at the files in ramdisk_tools folder. There are only the source code of device_infos.c and systemkb_bruteforce.c the problem is that i work under linux so i can not compile them. >gcc device_infos.c -o device_infos >device_infos.c:3:43: fatal error: CoreFoundation/CoreFoundation.h: File o directory non esistente compilation terminated may i ask you the favor to compile these files so i can execute them on the iphone? Thank you very much Original comment by andrei.m.@gmail.com on 10 Oct 2012 at 10:56.
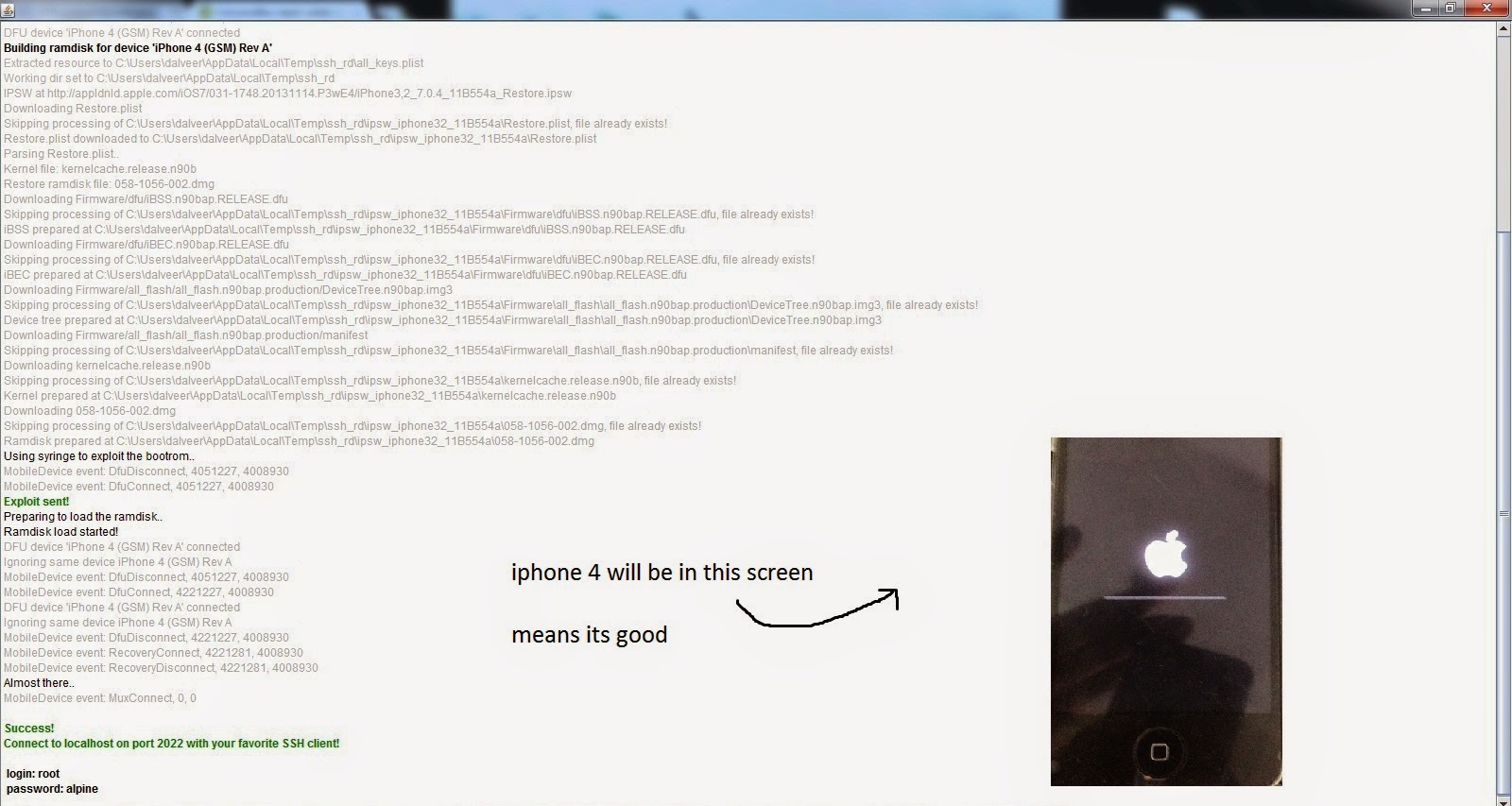
Download and install 2. Download and extract 3. Put your iPhone 4 into DFU mode (search on Google if you don't know how) 4. Start SSH.jar and wait until you see Success!
Written with green in the log there, also the iPhone will show the Apple logo with a grey horizontal line on its sreen 5. Open WinSCP and input, host name 127.0.0.1, port 2022, user name root, password alpine and press login 6. In WinSCP look for Terminal and open it, then execute command mount.sh, make sure the terminal says 'Mounting /dev/disk0s1s1 on /mnt1' and “Mounting /dev/disk0s1s2 on /mnt2' then close Terminal. In WinSCP right explorer pane, navigate to /Mnt1/Applications and delete Setup.app folder 8.
New News
- Elexia Comfort Manual Transfer
- Blaupunkt Radio Code Generator
- Bobcad Cam V21 Keygen Crack
- Primavera P6 Software Full Version With Crack
- Unlock Bootloader Exe
- Kalloori Movie Songs Free Download Starmusiq9760006
- Treker Torrent Knigi Loskutnoe Shitje
- Chertezhi Ruchnih Valjcov
- Raja Shiv Chhatrapati Marathi Serial Saraswati
- Unity 3d Car Script Files Download
- Adobe Lightroom Cracked Apk For Android
- Korolek Ptichka Pevchaya Noti